Github Action to Build Golden Images with HashiCorp Packer
In previous posts we have already shown multiple ways to use HashiCorp Packer to build Golden Images. In this post we will show how to automate the process with

In today's dynamic and complex cloud environments, organisations face significant challenges in managing costs while ensuring compliance and operational efficiency. As organisations scale their cloud usage, strategies to optimise cost management become more important than ever. Mondoo is a comprehensive security and compliance platform designed to help organisations automate and enforce security across their infrastructure, ensuring robust governance and operational efficiency. Mondoo can even help you track your active assets. This is where the use of resource tagging and the integration of custom Mondoo policies can make a significant difference.
Resource tagging, a powerful but often underutilised practice, allows organisations to systematically categorise and track their cloud resources. When combined with custom Mondoo policies, which provide a comprehensive approach to governance and compliance, organisations can achieve greater visibility, control and cost efficiency. In this blog, we will show you how to tag your Mondoo assets and create custom Mondoo policies to check for specific tags and their values.
Tagging proves valuable by offering a structured approach to categorizing, organising, and tracking items or assets. With tags, individuals or organisations can efficiently group related items, aiding in management, retrieval, and analysis. Tags are flexible, allowing customization based on various criteria like ownership, type, or location, enhancing productivity, collaboration, and decision-making through improved visibility and context within a system or dataset. By categorising assets with descriptive metadata, tags enable better visibility, cost management and compliance tracking, ultimately improving overall operational efficiency and control.
The easiest way to add metadata to a resource is through the Dashboard. Any asset can have one or more annotations added to it, providing an easy way to enrich data and improve insight. Note that most annotations added in the Dashboard cannot be queried with MQL, but can only be read manually by selecting the specific asset.
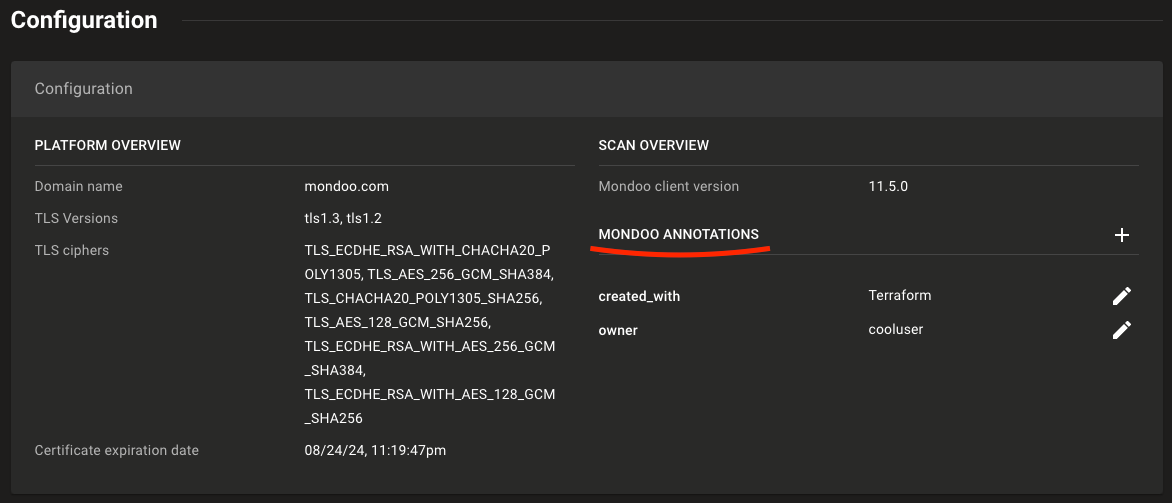
The next methods focus on adding tags directly to the resources, independently of Mondoo. This allows users to read these tags and create their own tracking policy using MQL. In cloud environments, for instance, tags are essential for organising and managing resources efficiently. To see which resources MQL can be used for reading tags or similar fields, visit the MQL documentation.
The process of adding metadata to resources can vary from provider to provider. In this case, we will focus on tagging resources within the cloud providers Azure and AWS, which will be relevant for Mondoo Integrations and can later be read by our custom MQL query. Note that tags can also be managed with the CLI tools of each provider.
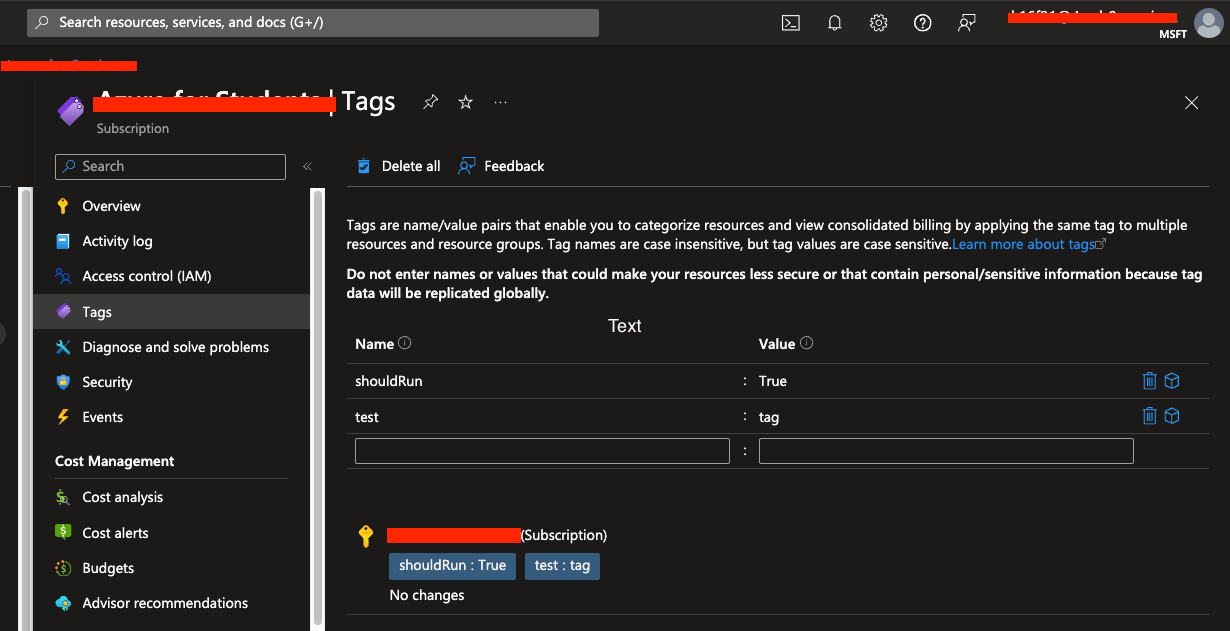
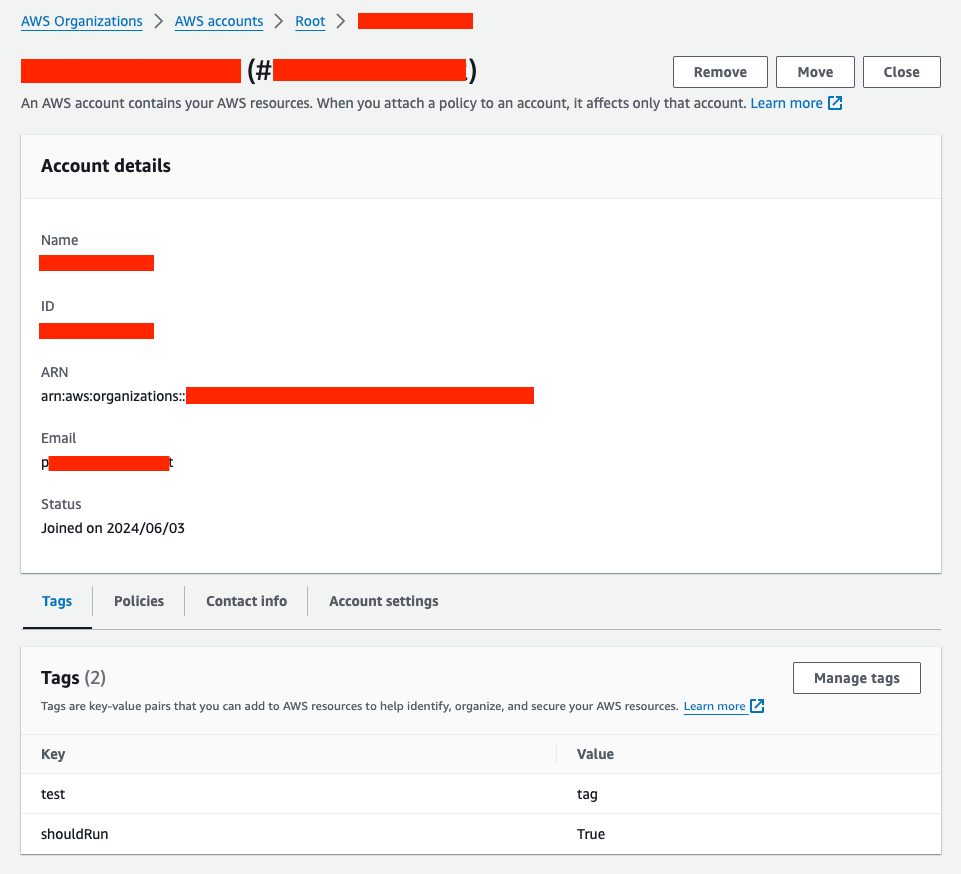
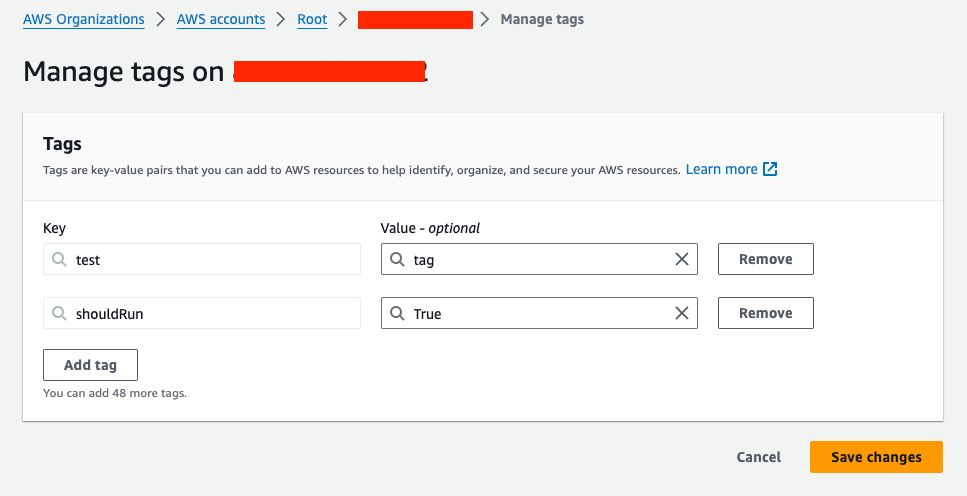
With Terraform, users can define and provision infrastructure using a high-level configuration language. This approach ensures that resource tags are consistently applied and maintained across environments. Let’s add tags directly after setting up our integrations for Mondoo.
If you're working with an existing infrastructure that was not initially tagged (a brownfield approach), you can use the
terraform importcommand to import the existing resources into your Terraform state. This allows you to manage and tag these resources as if they were originally created with Terraform.
azurerm_subscription resource, as Terraform will encounter an error when destroying. This is because Terraform treats the changes as if it needs to create a new resource rather than just updating the existing one. A third-party module is the solution. 1provider "mondoo" {
2 region = "eu"
3}
4# Create a new space
5resource "mondoo_space" "azure_space" {
6 name = "Azure Terraform Integration"
7 org_id = var.mondoo_org
8}
9# Setup the Azure integration
10resource "mondoo_integration_azure" "azure_integration" {
11 space_id = mondoo_space.azure_space.id
12 name = "Azure ${local.mondoo_security_integration_name}"
13 tenant_id = var.tenant_id
14 client_id = azuread_application.mondoo_security.client_id
15 scan_vms = true
16 # subscription_allow_list= ["ffffffff-ffff-ffff-ffff-ffffffffffff", "ffffffff-ffff-ffff-ffff-ffffffffffff"]
17 # subscription_deny_list = ["ffffffff-ffff-ffff-ffff-ffffffffffff", "ffffffff-ffff-ffff-ffff-ffffffffffff"]
18 credentials = {
19 pem_file = join("\n", [tls_self_signed_cert.credential.cert_pem, tls_private_key.credential.private_key_pem])
20 }
21 # wait for the permissions to provisioned
22 depends_on = [
23 mondoo_space.azure_space,
24 azuread_application.mondoo_security,
25 azuread_service_principal.mondoo_security,
26 azurerm_role_assignment.mondoo_security,
27 azurerm_role_assignment.reader,
28 ]
29}
1# https://registry.terraform.io/modules/qbeyond/subscription-tags/azapi/2.0.1
2module "subscription_tags" {
3 source = "qbeyond/subscription-tags/azapi"
4 version = "2.0.1"
5 subscription_id = var.primary_subscription
6 tags = {
7 "shouldRun" = "True"
8 }
9}
1variable "mondoo_org" {
2 description = "Mondoo Organisation"
3 type = string
4 default = "my-org-123456789"
5}
6variable "aws_access_key" {
7 description = "AWS access key"
8 type = string
9}
10variable "aws_secret_key" {
11 description = "AWS access key"
12 type = string
13}
14provider "mondoo" {
15 region = "eu"
16}
17# Create a new space
18resource "mondoo_space" "my_space" {
19 name = "AWS Terraform"
20 org_id = var.mondoo_org
21}
22# Setup the AWS integration
23resource "mondoo_integration_aws" "name" {
24 space_id = mondoo_space.my_space.id
25 name = "AWS Integration"
26 credentials = {
27 key = {
28 access_key = var.aws_access_key
29 secret_key = var.aws_secret_key
30 }
31 }
32}
1provider "aws" {
2 region = "eu-central-1"
3 default_tags {
4 tags = {
5 shouldRun = "True"
6 }
7 }
8}
9# Add a tag to the existing aws_organizations_account
10import {
11 to = aws_organizations_account.account
12 id = "1234567890"
13}
14resource "aws_organizations_account" "account" {
15 name = "My Account"
16 email = "myaccount@mail.com"
17 lifecycle {
18 prevent_destroy = true
19 }
20}
By using the brownfield approach, we can ensure that existing resources are brought under consistent management and tagging practices, which is essential for maintaining control and visibility in your cloud environment. To learn more about using Mondoo and Terraform together, check out our blogpost about integrating Mondoo with Terraform.
Mondoo policies are specifications used when scanning a system. They are essentially checklists that ensure a system is compliant with security and other best practices. These policies are expressed as highly readable code, which can be written in the Mondoo Query Language (MQL) or by using pre-defined policies provided by Mondoo.
By writing our own MQL query to look for tags of a particular asset or resource and wrapping it in a standalone policy, we can test a given resource to see if it contains the keys and values of the tags we want. The test can either pass or fail, signaling us if a resource is still current and properly categorised. This automated verification process ensures that all resources adhere to the tagging conventions set by the organisation.
How can we do that?
Let’s look at the examples from above and implement MQL queries for the Azure and AWS assets. The queries can be tailored to meet specific requirements. In this example, we test whether a specific tag is present and has the correct value.
azure.subscription.tags.contains('TAGNAME') && azure.subscription.tags["TAGNAME"] == "TAGVALUE"
aws.account.tags.contains('TAGNAME') && aws.account.tags["TAGNAME"] == "TAGVALUE"
These custom queries are not restricted to the asset types of the integration but can be customized to scan any resource within these accounts/subscriptions/assets. MQL Reference | Mondoo Docs
To write the actual Mondoo policy, you can follow this structure:
1policies:
2 - uid: check-for-tags-XY
3 name: Check for Tag XY
4 version: 1.0.0
5 scoring_system: highest impact
6 authors:
7 - name: Your Name
8 email: your@main.com
9 docs:
10 desc: |-
11 Ensure that resources have the required tag. If a resource is missing a tag, the check will fail.
12 groups:
13 title: Identity and Access Management
14 filters: |
15 asset.platform == "<PROVIDER_PLATFORM>" # e.g. "azure", "aws"
16 asset.kind == "api"
17 checks:
18 - uid: check-for-tag-mql-X
19queries:
20 - uid: check-for-tag-mql-X
21 title: Resource Tagging
22 impact: 100
23 mql: |
24 <YOUR_MQL_QUERY>
Note that the file for configuring custom policies must be of type
.mql.yaml.
Once the policy file has been created, it can be uploaded to Mondoo for activation. We can either do this by uploading it via the dashboard or Terraform.
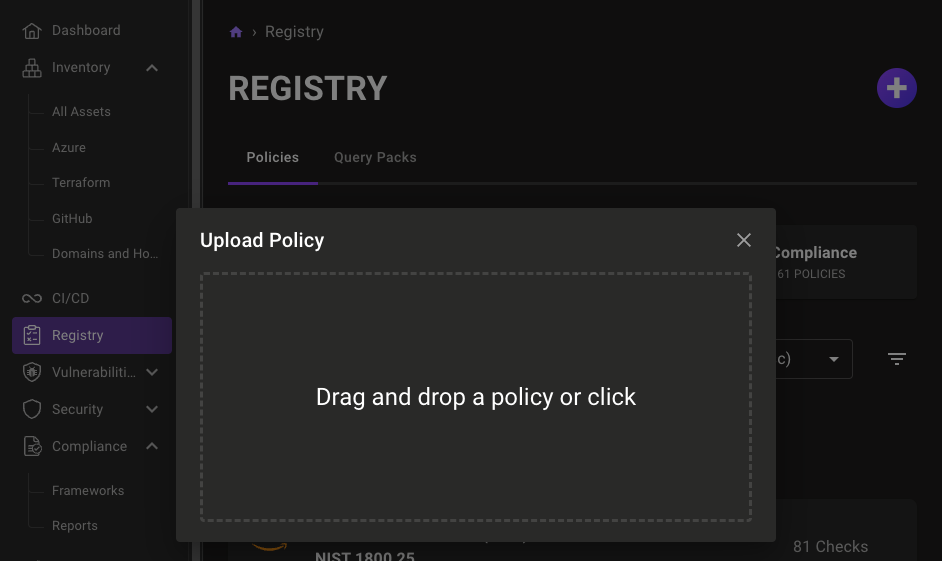
mondoo_custom_policy and mondoo_policy_assignment resources: 1variable "my_custom_policy" {
2 description = "Path to the custom policy file. The file must be in MQL format."
3 type = string
4 default = "policy.mql.yaml"
5}
6
7resource "mondoo_custom_policy" "my_policy" {
8 space_id = mondoo_space.my_space.id
9 source = var.my_custom_policy
10 overwrite = true
11}
12
13resource "mondoo_policy_assignment" "space" {
14 space_id = mondoo_space.my_space.id
15
16 policies = concat(
17 mondoo_custom_policy.my_policy.mrns,
18 [],
19 )
20
21 state = "enabled"
22
23 depends_on = [
24 mondoo_space.my_space
25 ]
26}
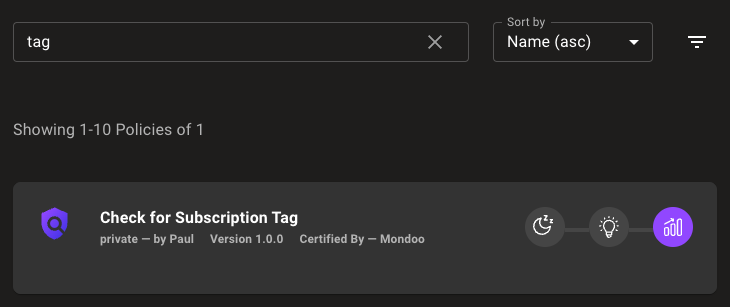
When a new scan has been triggered, the policy should appear in the corresponding asset entry. We are now able to manage our assets with the help of Mondoo tags. If an asset is missing a specified tag, we can immediately identify it in the scan results. The policy will flag the asset and return a bad score, indicating non-compliance.
For instance, if we have a policy that checks for a specific tag on an AWS EC2 instance, and the instance is missing this tag, the policy will flag this non-compliance and assign a failing grade. In addition, notifications for changing asset results can be activated. This immediate feedback allows administrators to quickly identify and address tagging issues, ensuring that all assets comply with organizational standards.
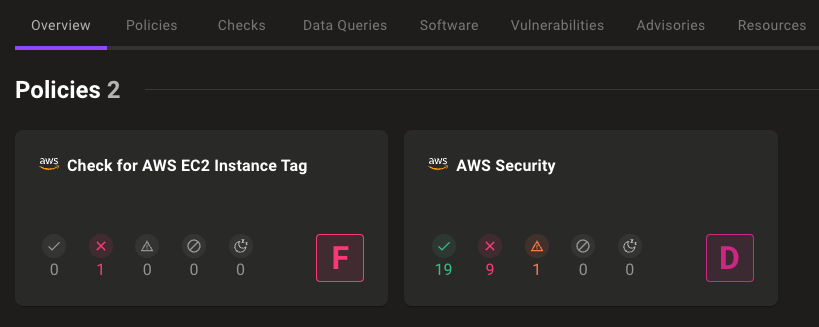
By taking corrective action, such as updating the asset's tags or removing the flagged resource to meet the required criteria, we ensure that all assets are properly tagged and compliant with our organizational standards, improving overall asset management and governance.
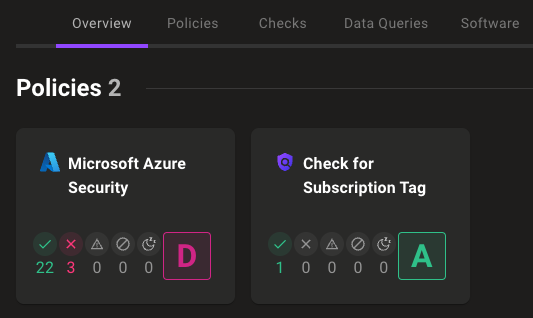
If you want to know more about custom policies, check out our blogpost about writing custom policies for Mondoo.
In conclusion, managing cloud costs and ensuring compliance in dynamic environments is a complex challenge. Mondoo's comprehensive security and compliance platform, combined with strategic resource tagging and custom policies, significantly enhances visibility, control, and efficiency. Tagging resources allows systematic categorization and tracking, while custom Mondoo policies ensure adherence to organisational standards. By integrating these practices, organisations can automate compliance checks, promptly address non-compliance issues, and maintain robust governance across their cloud infrastructure. This holistic approach ultimately leads to improved operational efficiency and cost management.
You are interested in our courses or you simply have a question that needs answering? You can contact us at anytime! We will do our best to answer all your questions.
Contact us