Is Atlantis a Viable Alternative to HashiCorp Cloud Platform Terraform?
Infrastructure as Code (IaC) has revolutionized the way organizations manage cloud infrastructure, with Terraform leading as a premier tool. HashiCorp Cloud

In the ever-evolving landscape of cloud infrastructure management, efficiently securing and monitoring resources is critical. This is where Mondoo comes in, a powerful security and compliance platform. With Mondoo, it is possible to reveal vulnerabilities, lost assets, and policy violations before they become exploits.
Creating Mondoo resources with Terraform enables organisations to manage their security infrastructure as code, leveraging Terraform's capabilities for Infrastructure as Code (IaC), version control, automation, scalability, and consistent security posture. By defining Mondoo resources in Terraform configuration files, teams can automate the provisioning and management of Mondoo agents, policies, scans, and other security components. This approach facilitates collaboration, integration with CI/CD pipelines, and ensures that security configurations are consistently applied across different environments, reducing the risk of misconfigurations and enhancing overall security governance within cloud-native environments.
This guide will show you how to create a new space in your organisation and how to add integrations and policies to it.
The following prerequisites are necessary to follow along with this guide:
MONDOO_API_TOKEN: Can be obtained in your Mondoo organisation Settings → API TokensMONDOO_CONFIG_BASE64: Can be obtained in your Mondoo Organisation Settings → Service Accounts → Generate new Service Account with Editor permissionsTo create Mondoo integrations with Terraform, you will need the Terraform Mondoo Provider.
.tf file, such as main.tf, in your workspace. In this file, you can reference the Mondoo provider and configure your integration resources. Below is an example of how to set up the Mondoo provider in your Terraform configuration: 1# main.tf
2terraform {
3 required_providers {
4 mondoo = {
5 source = "mondoohq/mondoo"
6 version = ">= 0.4.0"
7 }
8 }
9}
10
11provider "mondoo" {
12 region = "us" # use "eu" for the European region
13}
Add policies to your integration. You can browse and copy the policy URI in the Registry tab of your organisation. (e.g. https://console.mondoo.com/space/registry/namespace/mondoohq/policies/mondoo-aws-security?spaceId=xxx)
The example below demonstrates how a policy can be assigned. For your integrations, you can create a second .tf file, such as resources.tf.
1# resource.tf
2resource "mondoo_policy_assignment" "policies" {
3 space_id = mondoo_space.my_space.id
4
5 policies = [
6 "//policy.api.mondoo.app/policies/mondoo-security-policy"
7 ]
8
9 state = "enabled" # default is enabled, we also support preview and disabled
10
11 depends_on = [
12 mondoo_space.my_space
13 ]
14}
MONDOO_API_TOKEN and MONDOO_CONFIG_BASE64 in your terminal or use it as variables in your HCP Terraform workspace.terraform apply! You will be asked to provide your organisation's id, which can be found in the settings of your organisation.In this example, the Domain integration is created using Terraform, along with a new Space and appropriate policies. A Space is a logical grouping of specific assets (such as AWS accounts or workstations). A Space can contain many integrations with corresponding assets that contain information about their security score. To receive a score, an asset needs policies that contain individual tests to be checked against. Policies are enabled or disabled for the whole space.
The Domain Resource has the following Schema:
Required
host (String) Domain name or IP address.space_id (String) Mondoo Space Identifier.Optional
http (Boolean) Enable HTTP port scan.https (Boolean) Enable HTTPS port scan.Read-Only
mrn (String) Integration identifierTerraform resource file:
1# resource.tf
2variable "mondoo_org" {
3 description = "The Mondoo organisation ID"
4 type = string
5}
6
7provider "mondoo" {
8 region = "us"
9}
10
11# Create a new space
12resource "mondoo_space" "domain_space" {
13 name = "My Domain Name"
14 org_id = var.mondoo_org
15}
16
17# Setup the Domain integration
18resource "mondoo_integration_domain" "domain_integration" {
19 space_id = mondoo_space.domain_space.id
20 host = "example.com"
21 https = true
22 http = false
23}
24
25# Assign policies for Domain integration
26resource "mondoo_policy_assignment" "policies" {
27 space_id = mondoo_space.domain_space.id
28
29 policies = [
30 "//policy.api.mondoo.app/policies/mondoo-http-security",
31 "//policy.api.mondoo.app/policies/mondoo-dns-security",
32 "//policy.api.mondoo.app/policies/mondoo-tls-security"
33 ]
34
35 state = "enabled" # default is enabled, we also support preview and disabled
36
37 depends_on = [
38 mondoo_space.domain_space
39 ]
40}
After applying the terraform configuration (run terraform apply if you use Terraform via the CLI), go to your Mondoo Spaces overview to check that a new space has been successfully created.
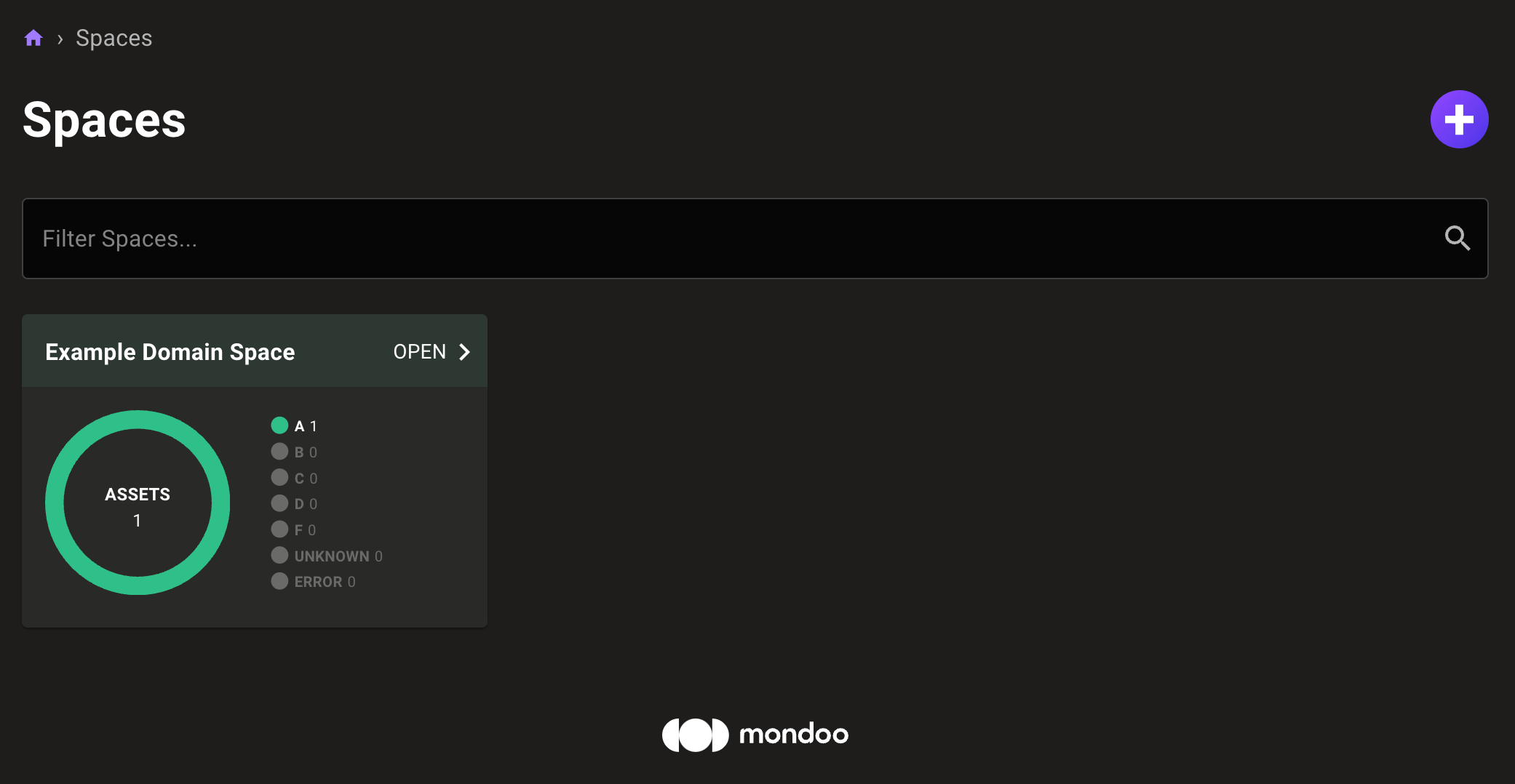
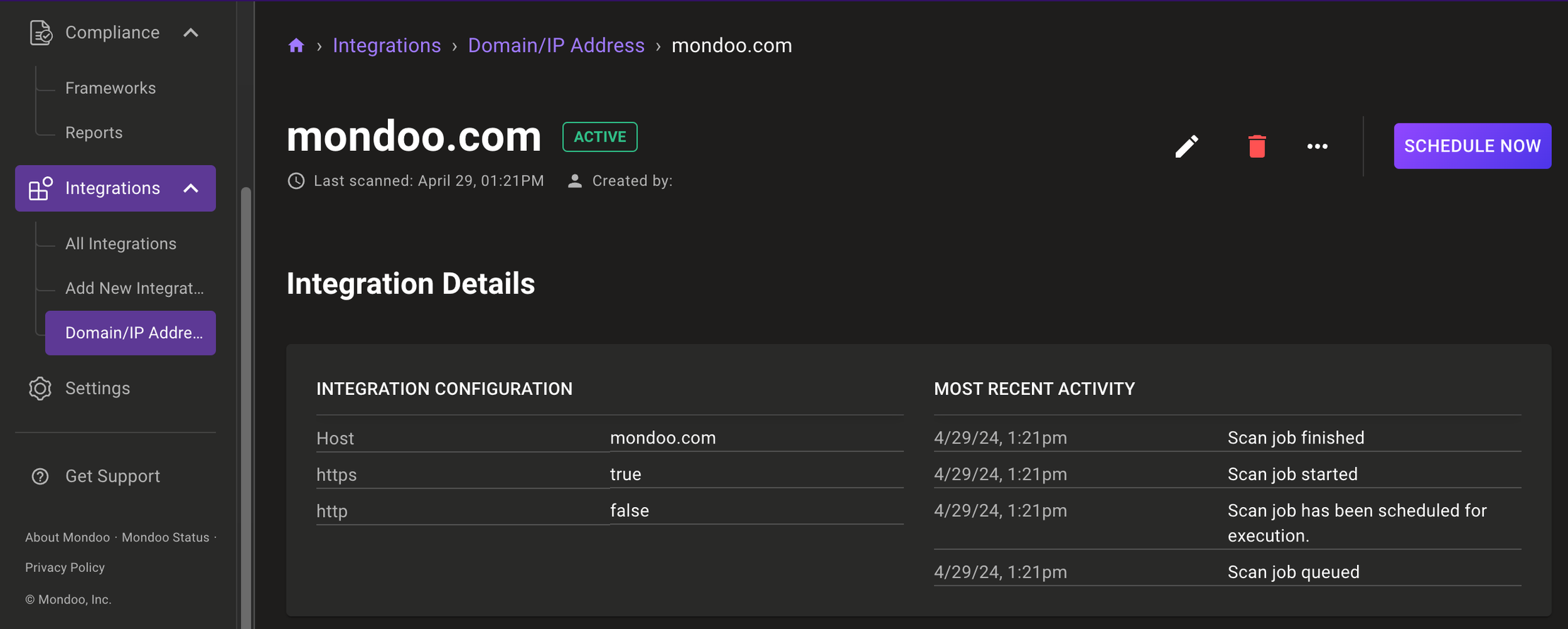
Within the space, you will see your new integration under the Integrations tab. Click on it to see your configuration options and any automatically scheduled scans.
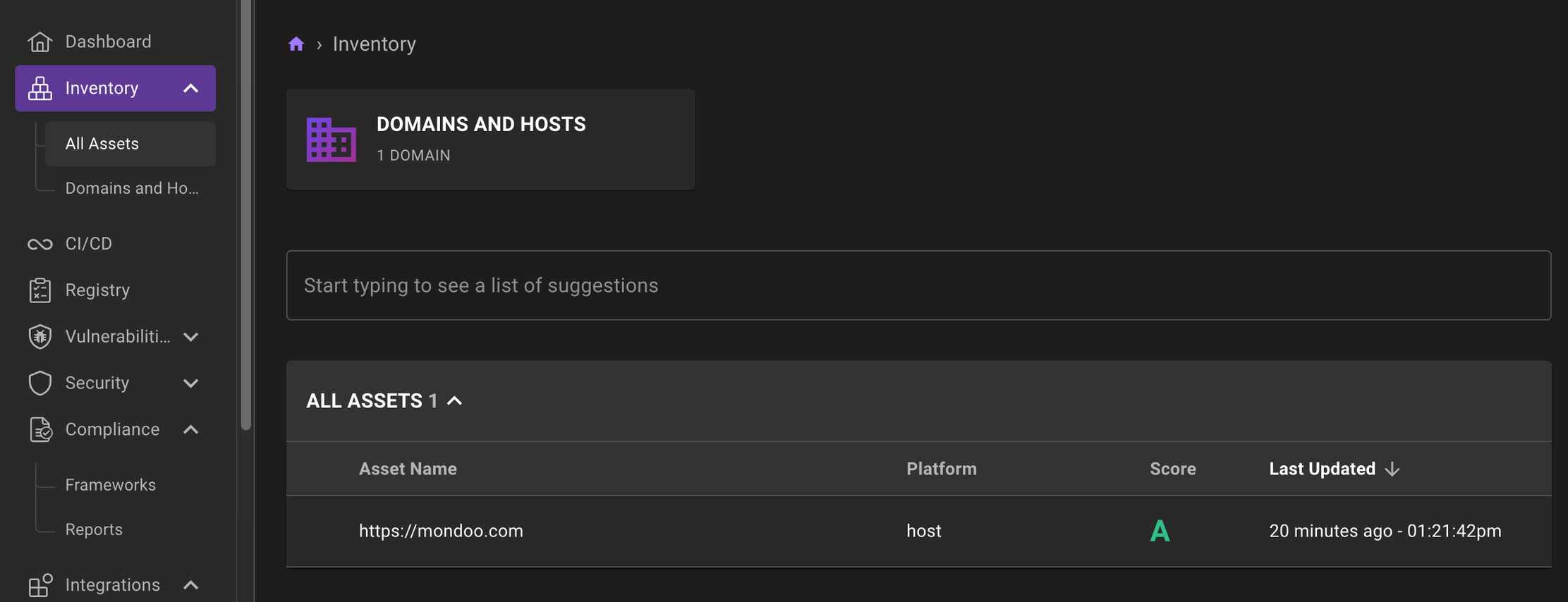
The actual asset, with all its test results and policies, can be found in the Inventory tab. Here you can view your asset's current security score, monitor any failed policy checks and get tips on how to mitigate risks.
In conclusion, Mondoo, coupled with Terraform, offers a robust solution for managing security and compliance in cloud infrastructure. By seamlessly integrating Mondoo resources into Terraform configurations, organisations can automate the deployment and management of security components, ensuring consistent security posture across different environments. This approach not only enhances efficiency but also reduces the risk of vulnerabilities and policy violations going unnoticed. By following the steps outlined in this easy guide, organisations can establish a solid foundation for proactive security governance within their cloud-native environments. With Mondoo and Terraform, organisations can stay ahead of potential exploits and maintain a strong security stance in the ever-evolving landscape of cloud infrastructure management.
You are interested in our courses or you simply have a question that needs answering? You can contact us at anytime! We will do our best to answer all your questions.
Contact us