Is Atlantis a Viable Alternative to HashiCorp Cloud Platform Terraform?
Infrastructure as Code (IaC) has revolutionized the way organizations manage cloud infrastructure, with Terraform leading as a premier tool. HashiCorp Cloud


This is the first post in a series about IT compliance with Mondoo. This post will focus on the basics of Mondoo and how you can use it to get insights about any security vulnerabilities that might be hiding inside your IT-infrastructure landscape.
To demonstrate, I will be creating infrastructure with the help of HashiCorp Terraform on Microsoft Azure cloud. Then, I will integrate Mondoo with a Microsoft Azure account (aka "subscription"), and the infrastructure resources as well, to continuously check for IT compliance.
Continuous IT compliance is an approach that emphasizes real-time monitoring and proactive management of an organization's IT systems to ensure adherence to relevant regulations, standards, and security practices. Unlike traditional periodic audits, continuous IT compliance involves ongoing assessment and adjustment of IT processes, policies, and controls.
This dynamic and iterative process enables organizations to promptly identify and address compliance issues, reducing the risk of non-compliance incidents. Automation plays a crucial role in continuous IT compliance! Tools like Mondoo will help you stay compliant.
Mondoo is brought to you by the team who gave you InSpec/ServerSpec and the DevSec project. It is a software tool that will continuously assesses the security of your IT infrastructure. It will do this, on the basis of "policies".
Policies are rules that you define about your IT infrastructure eg. "the SSH port is never allowed to be open". Mondoo policies are written as high-level code that automates security compliance and best practices.
However, not all policies need to be written by yourself. Mondoo already comes with tons if pre-written policies based on international security best practices!
Checkout the official Mondoo website to learn more.
Now that you understand what compliance and Mondoo is, it is time demonstrate what it can do. To check for compliance issues, we need IT infrastructure. I will use HashiCorp Terraform to provision that infrastructure inside a Microsoft Azure Cloud account/subscription.
If you are not familiar with HashiCorp Terraform, make sure to read this post, visit this website or checkout our foundations course.
The Terraform code I am using can be found inside a public GitHub repository. For this demonstration, only the "non-compliant" subdirectory is relevant.
If you want to follow along, make sure to create Mondoo account, install Terraform, clone the GitHup repository, login to your Azure account and then run the following commands inside the cloned repo:
1$ cd non-compliant
2$ terraform init
3$ terraform apply
As a result, your Azure account contains now a virtual machine running Ubuntu Linux 20.04 LTS. The machine is also running a small NodeJS web application that is available on port 80. You can also connect via SSH to the VM by using the username "adminuser" and the password "$uperSecret1".
I have included some security vulnerabilities and bad practices on purpose. Do not use this code as baseline for secure IT infrastructure.
Inside your Mondoo account, select "Integrations" and then "Ubuntu/Debian". The UI will show you all the steps necessary to integrate the VM with Mondoo:
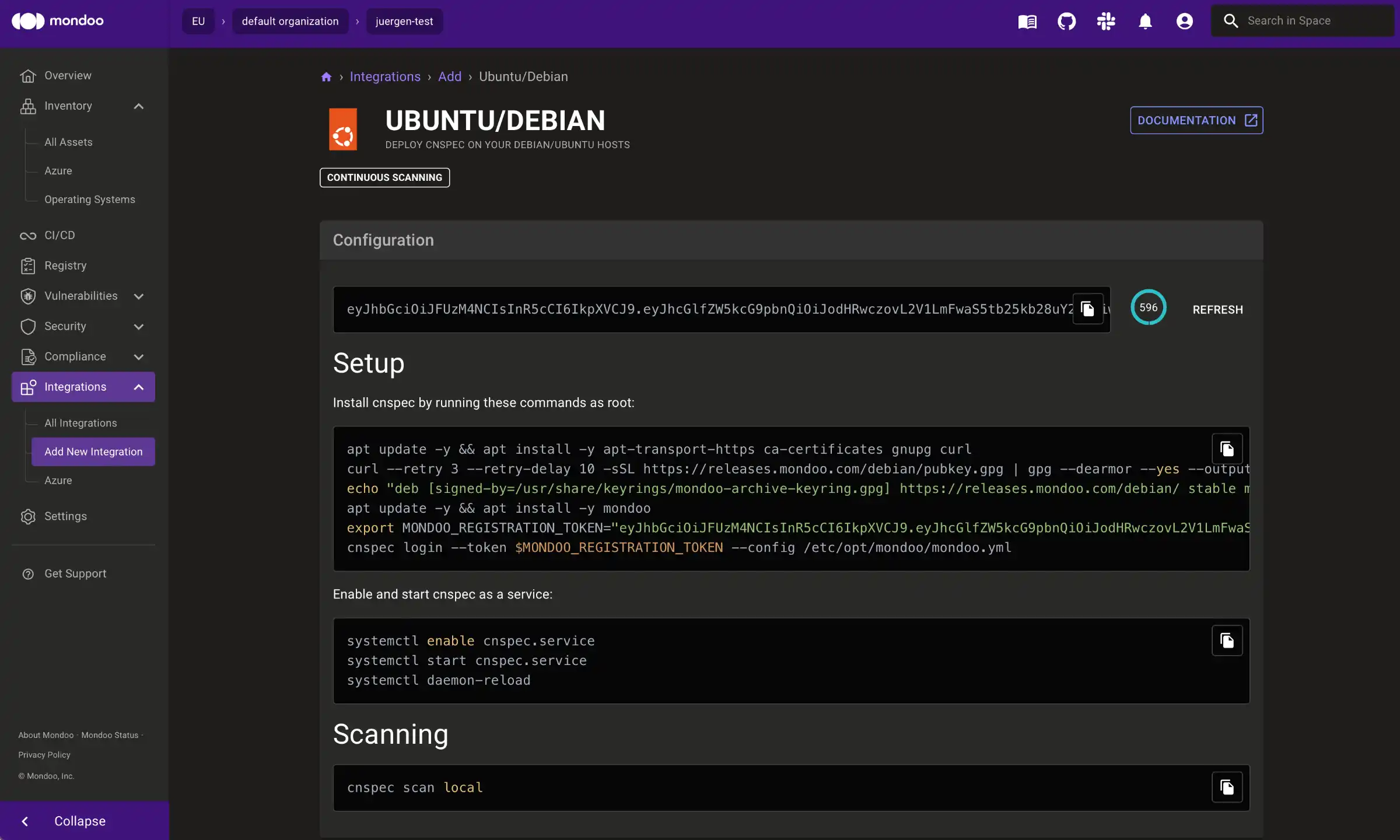
In a professional context, one would try to automate these steps inside the creation process of the VM itself. For this example, we use the manual steps to make them visible:
First, we install the Mondoo client (cnspec) on the VM by following the steps form the UI (as root):
1$ apt update -y && apt install -y apt-transport-https ca-certificates gnupg curl
2$ curl --retry 3 --retry-delay 10 -sSL https://releases.mondoo.com/debian/pubkey.gpg | gpg --dearmor --yes --output /usr/share/keyrings/mondoo-archive-keyring.gpg
3echo "deb [signed-by=/usr/share/keyrings/mondoo-archive-keyring.gpg] https://releases.mondoo.com/debian/ stable main" | tee /etc/apt/sources.list.d/mondoo.list
4$ apt update -y && apt install -y mondoo
5$ export MONDOO_REGISTRATION_TOKEN="<YOUR-TOKEN>"
6$ cnspec login --token $MONDOO_REGISTRATION_TOKEN --config /etc/opt/mondoo/mondoo.yml
Then we setup cnspec as a service. This will make sure that cnspec will scan this VM on a continuous basis:
$ systemctl enable cnspec.service
$ systemctl start cnspec.service
$ systemctl daemon-reload
As a last command, we trigger the first scan:
$ cnspec scan local
You should see a compliance analysis of the VM as command line output. However, the best way to review this data is through the UI. You should find a new entry in your inventory called "mondoo-demo-webserver-non-compliant" (that is the name we gave the VM):
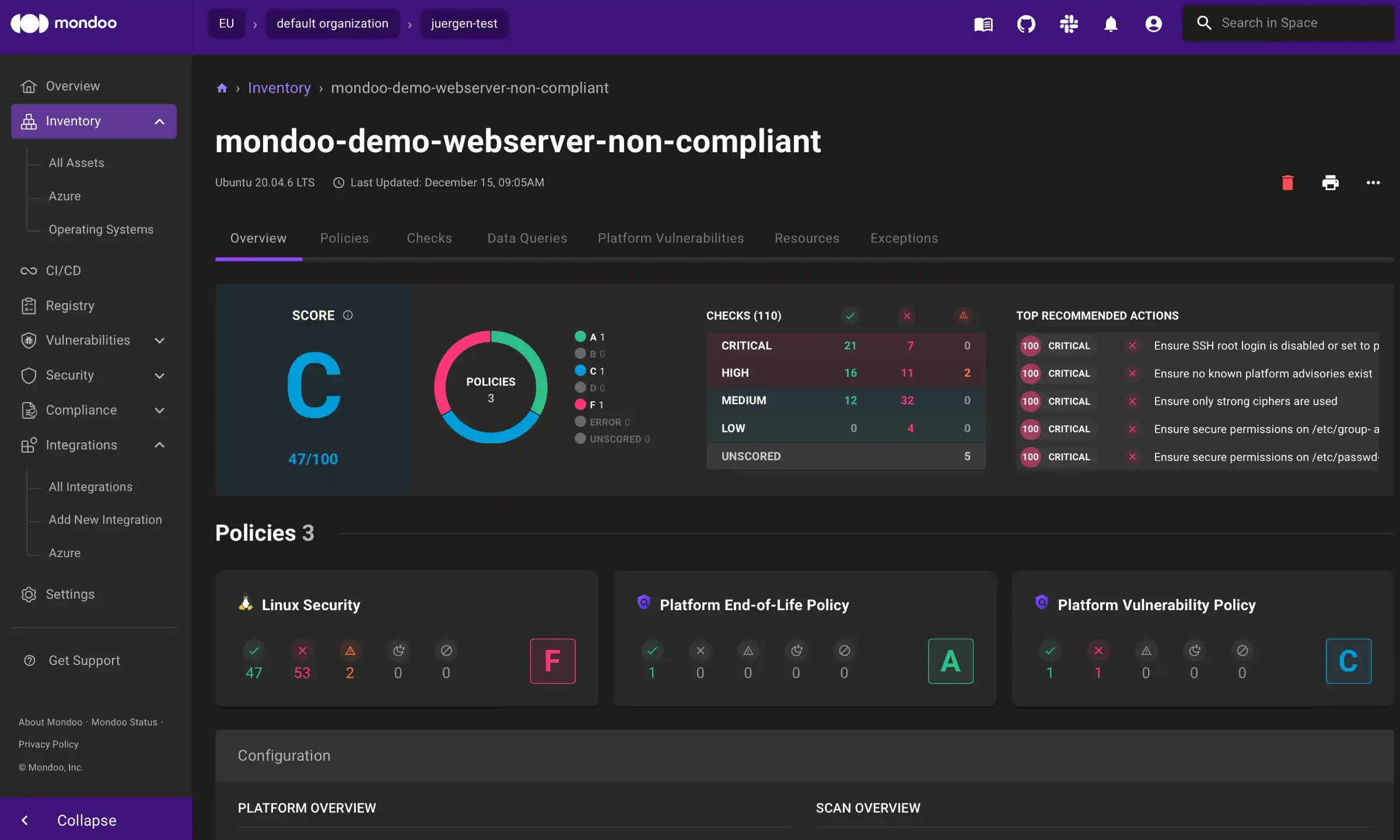
Mondoo uses it's included best-practice policies to rate this VM with a score of "C" (47/100 points). There are a lot of security issues on this VM!
If you click the "Checks" tab, you can see all of them listed there:
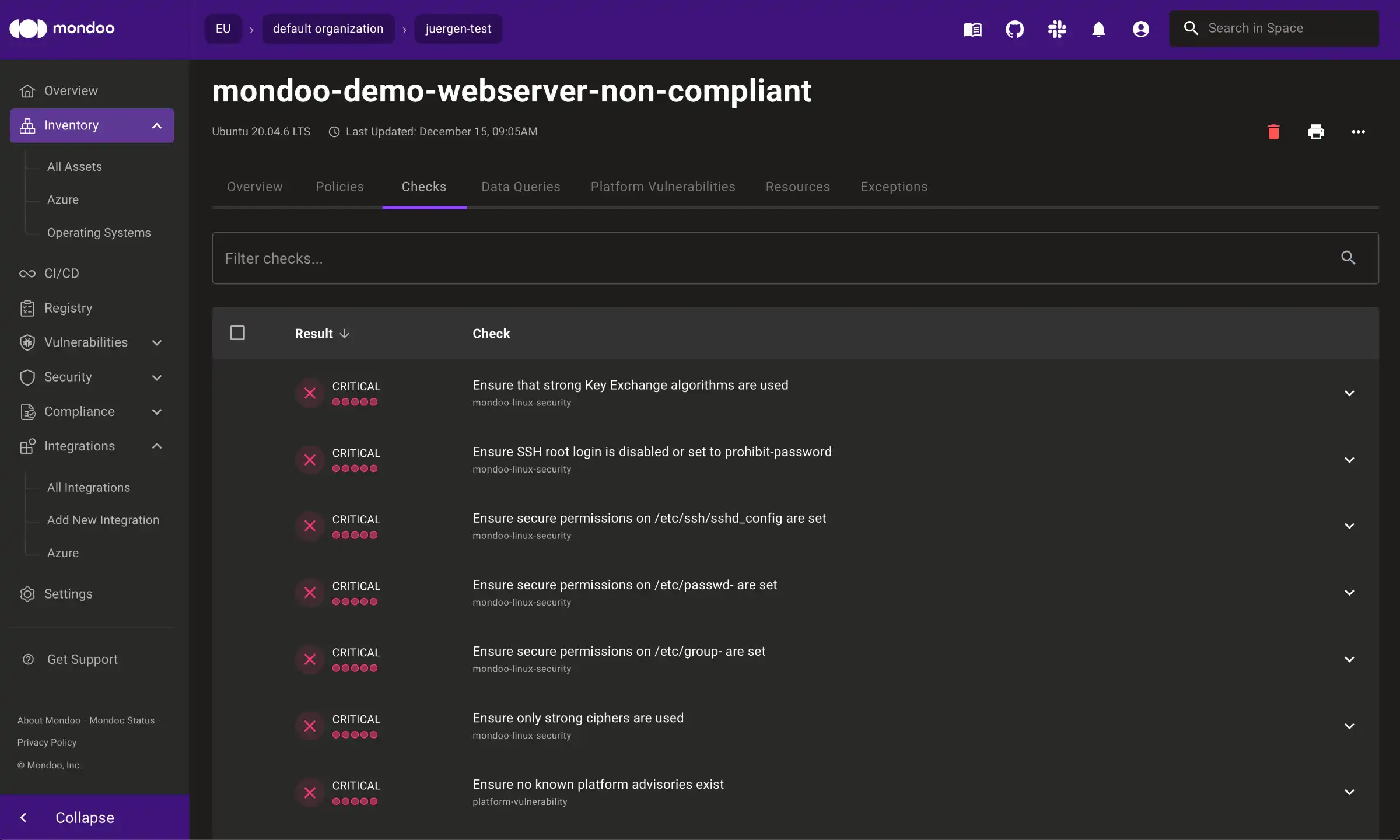
You can inspect each vulnerability and find helpful tips on how to remediate it:
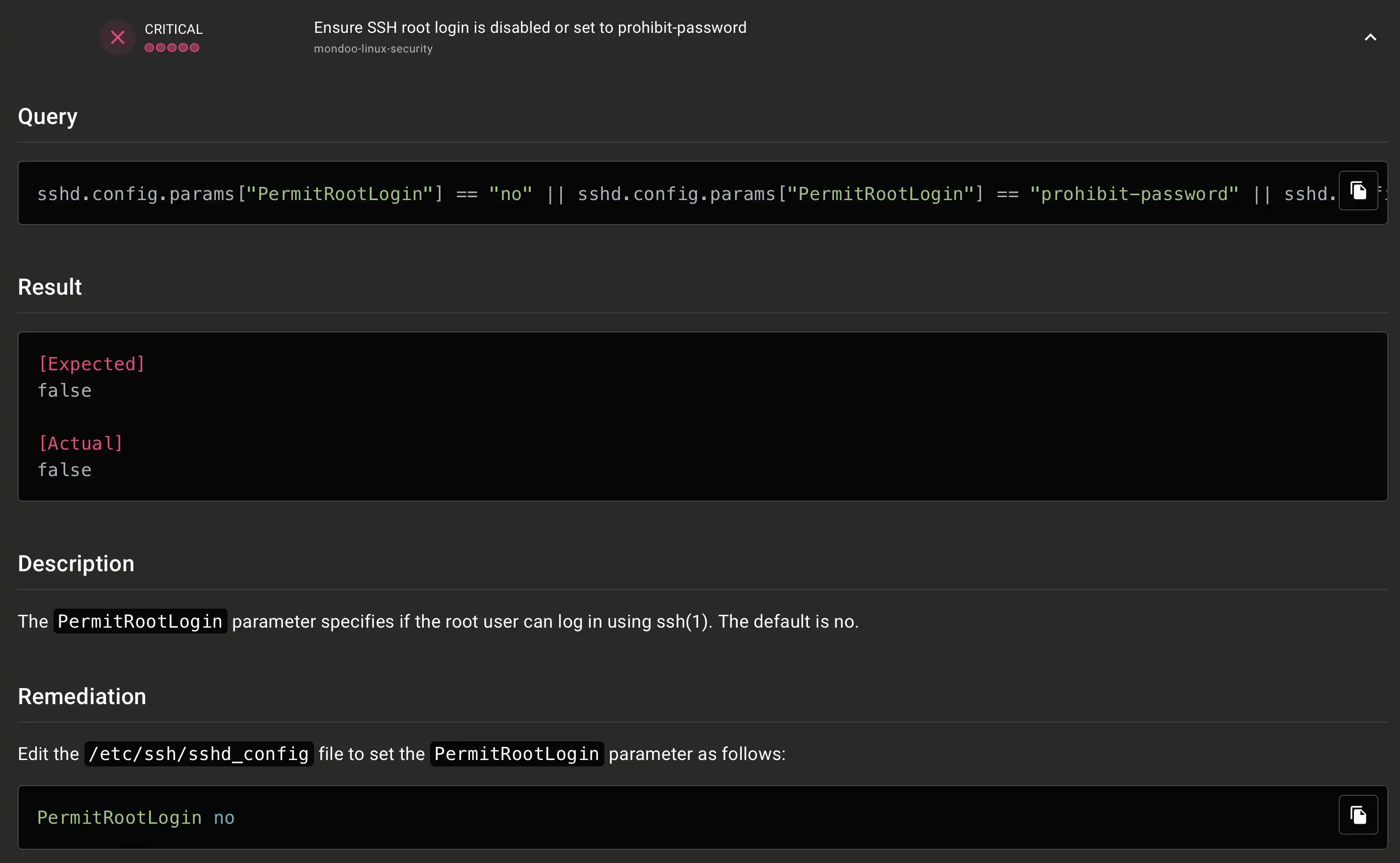
A future post will focus on fixing these vulnerabilities. For some of the vulnerabilities, a fix can be achieved by updating the operating system to the newest Ubuntu LTS version. Feel free to update the Terraform code to use a newer version and scan the VM again.
Checking a specific VM is great. However, Mondoo can also integrate with your whole Microsoft Azure account/subscription! There are quite some steps necessary to achieve this. The good news: Mondoo's documentation is excellent and has you covered! To integrate Mondoo and Azure, simply follow these steps described here.
One you have accomplished this, you will be able to see the scan results in your Mondoo dashboard as well:
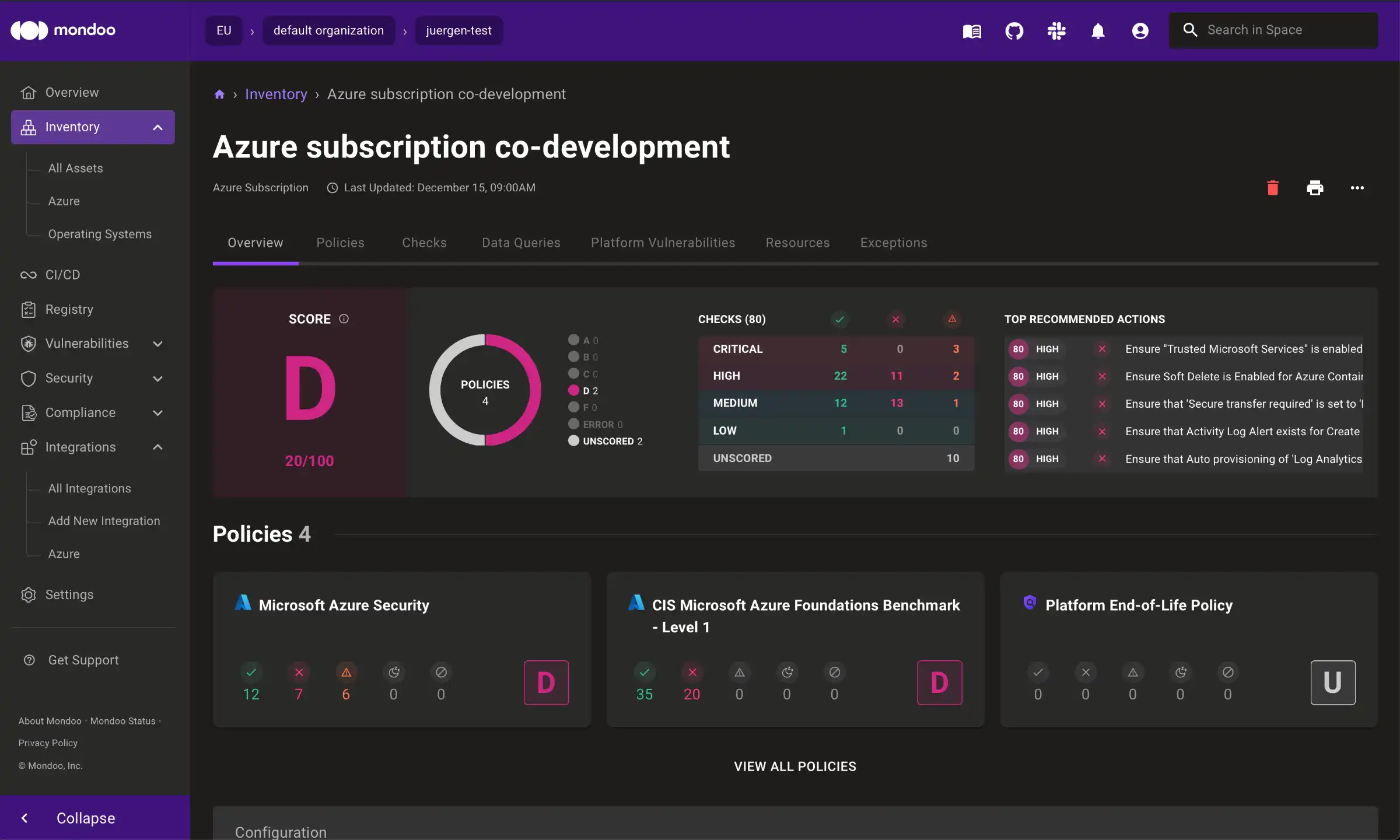
As you can see, we will also need to fix a lot of issues here! A "D" score (20/100 point) is nothing to be happy about.
Mondoo is a great tool for continuously checking for IT compliance. The included policies enable us to quickly set a secure base-line for our IT security. I am also a big fan on the UI. Everything is nicely organised and looks very good.
In the next post, I will try to remediate the security issues that I discovered in this post.
Future posts will also show how to write your own Mondoo policies and how to use Mondoo's CLI tools for checking our infrastructure code for compliance issues.
You are interested in our courses or you simply have a question that needs answering? You can contact us at anytime! We will do our best to answer all your questions.
Contact us